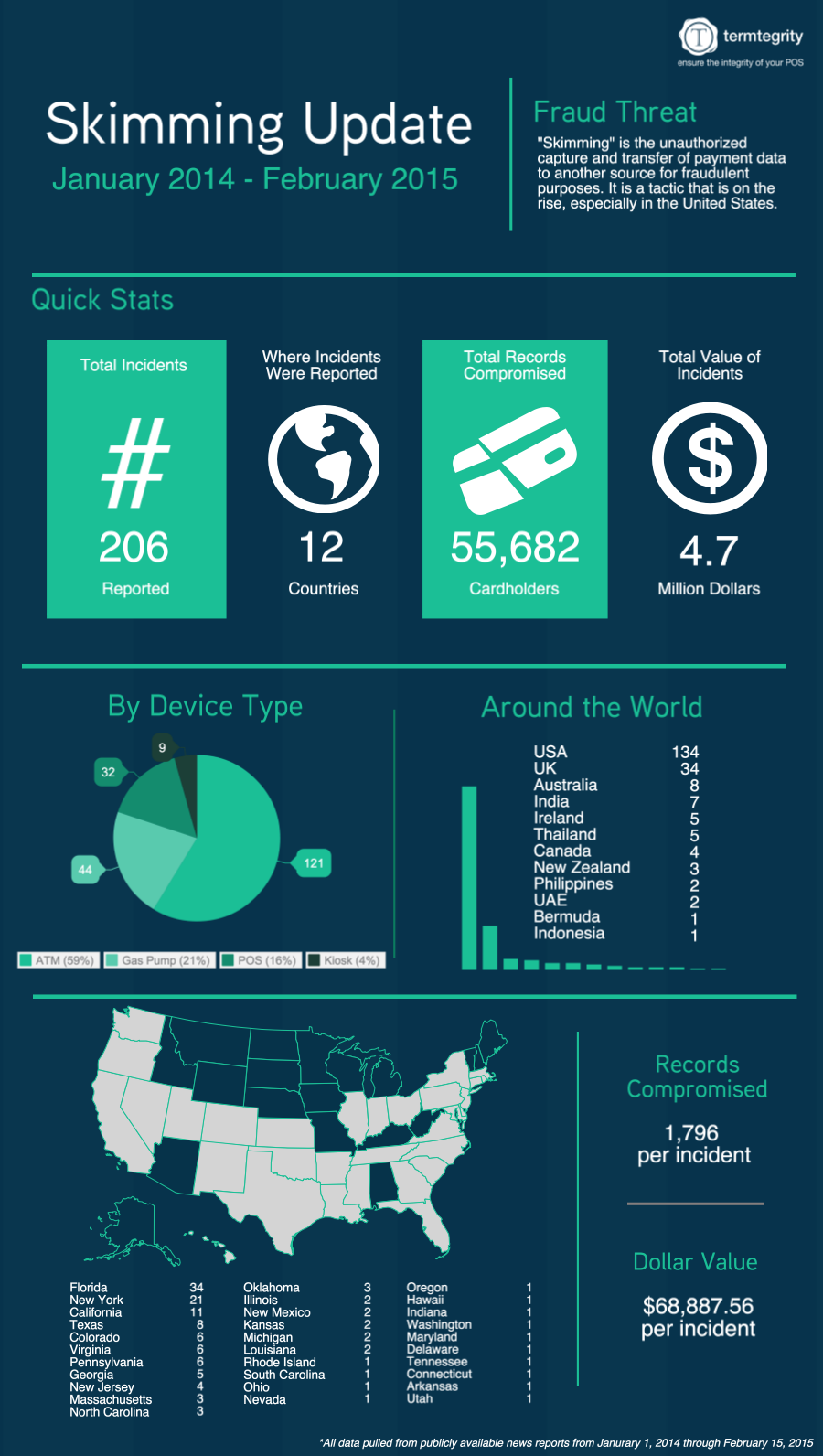
Remember that old adage about "teaching a person to fish?" That's pretty much what the third and final subsection of the new PCI DSS requirement 9.9 covers.
The 9.9.3 requirement states:
Provide training for personnel to be aware of attempted tampering or replacement of devices. Training should include the following:
- Verify the identity of any third-party persons claiming to be repair or maintenance personnel, prior to granting them access to modify or troubleshoot devices. granting them access to modify or troubleshoot devices.
- Do not install replace or return devices without verification.
- Be aware of suspicious behavior around devices (for example, attempts by unknown persons to unplug or open devices).
- Report suspicious behavior and indications of device tampering or substitution to appropriate personnel (for example, to a manager or security officer).
There are a few things here to consider.
- In order to provide training to employees, a formal policy is needed
- The formal policy isn't just written down, but is also disseminated to all the relevant employees; in this case, the front line employees
- Perhaps bundling this in your store's Standard Operating Procedure is a great way to start
When thinking about creating policy and training, they will need to cover scenarios such as:
- Will you ask front line employees to check the ID of the human who shows up to work on a device or ask them to call a manager?
- How does the manager know whether or not the person is supposed to be there?
- What does "suspicious behavior" mean?
- What is the mechanism for employees to report this suspicious behavior?
- What are the review and actions based on these reported incidents?
- Who is responsible, and accountable for them?
For this requirement, just ensuring your security staff is aware is not enough. In order for it to be effective, each person that works in a location where customers can swipe their credit cards needs to have read and acknowledged this policy and be trained on how to implement it. For this, there are several alternatives:
- If you already have a training program in place around PCI compliance and a procedure for updating the content, creating and adding a section on requirement 9.9 should suffice.
- There are organizations like our partner LiquidNexxus that are PCI certified trainers who also can create custom training for your organization.
- In SpotSkim, we've added both policy and training into the app. This allows for easy dissemination of information and tracking as the employee reviews and acknowledges both the policy and training.
Once you have created and rolled out the policy and training, the testing procedure for your QSA is to review the training and ensure it includes everything stated in the requirement. Once they validate the training, the QSA will select a sample of employees to interview to ensure they understand the policy and procedures found in the training.
Tracking and being able to report on when employees were presented with the policy and training will make this process much easier.
If you'd like to hear more about the requirement or have questions, Coalfire is hosting a webinar on April 28, 2015 at 2pm Eastern to review requirement 9.9 and answer attendee inquires. You can register for the session here.