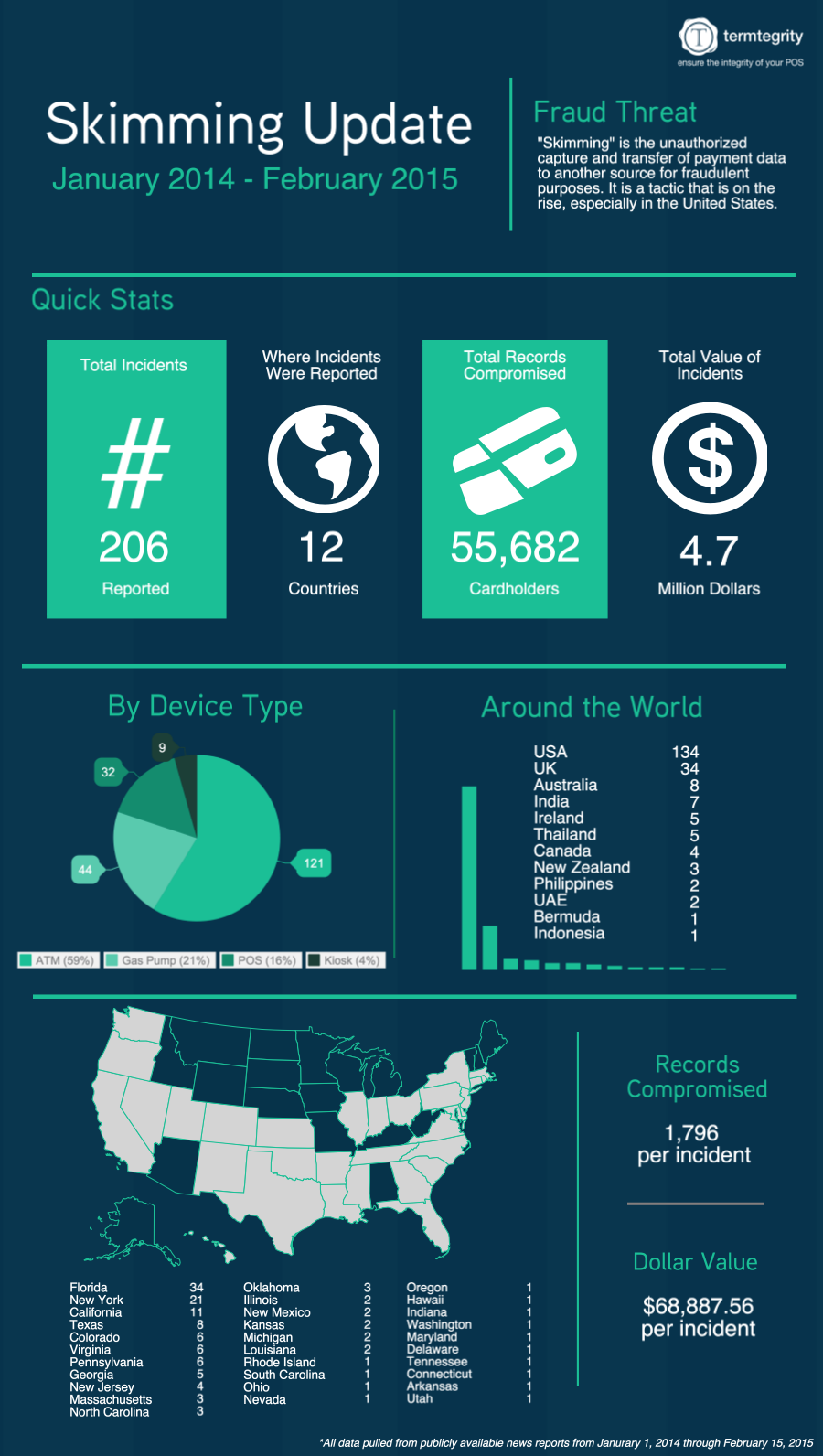
Last week, I posted the first in a three part series on the new PCI DSS 3.0, requirement 9.9. This addition to the DSS 3.0 is a best practice until June 30, 2015, after which it becomes enforceable for compliance.
Today's post is all about the second sub-requirement, 9.9.2, which covers device inspection.
In several product demonstrations I’ve done recently, the customers have remarked something similar to:
“Boy, that sounds like a lot of work. Do we actually have to inspect every device?”
The answer to that question is an emphatic yes. The best way to ensure no tampering is happening is by having a human look at each device to confirm:
1) It is in your inventory
2) It is in the location where you expect it to be
3) It is free of any signs of tampering
Here's what the actual requirement states:
9.9.2 = INSPECTION
Periodically inspect device surfaces to detect tampering (for example, addition of card skimmers to devices), or substitution (for example, by checking the serial number or other device characteristics to verify it has not been swapped with a fraudulent device).
The word “periodically” here can be read as “regular” and “consistent.” This is because if the devices aren’t being inspected on a set schedule, in the same way each time, inconsistencies across these checks could cause important signs of tampering to be missed.
Now, how to figure out what is the correct period of the inspections?
The SSC has provided a nice resource to help you figure out at exactly what frequency you should be inspecting your devices in the "Skimming Prevention: Best Practices for Merchants" document. Appendix A, starting on page 30, is a questionnaire that will assist in assessing the risk (high/medium/low) of a particular location which then corresponds with a timeframe.
Coalfire's "Complying with PCI-DSS Requirement 9.9" white paper provides a baseline recommendation on what a high/medium/low risk should translate into in terms of frequency. Their recommendations are daily for a high risk location, weekly for a medium risk, and monthly for a low risk.
Your particular location or business type may call for tweaking this reccomendation - for example, some gas merchants might choose to inspect at each shift change (their business type is a well known target for skimming). At the end of the day, you'll have to justify your choice of frequency to your QSA.
Then how do you make each inspection consistent?
There are two ways. The first is by utilizing highly skilled, security-focused employees who know exactly what to look for and how to go about inspecting devices.
The second is to create a template for inspection (an example is provided in Appendix B of the Skimming Prevention document) that walks the inspector through each step and highlights what they need to look for. This allows anyone in your organization to perform the inspections at any time. If data is collected in the right way around each inspection, then everything is available for that highly skilled security employee to review, if necessary.
So what about the actual inspection?
First, you'll want to check the device's unique identifier to confirm what you're looking at is the asset you think it is.
Once this is confirmed, next is checking for any tampering.
There are different places on each device type that are points of attack. For example, on a gas pump you would want to check the card swipe/dip, the receipt door, maintenance door, and PIN pad. Or if using a system like a Clover or Ziosk, which utilize encrypting readers, the only point of attack - thus the only point needing inspection - is the card swipe. On your particular set of assets, it is important to identify and inspect these areas of that are weak against attacks, as well as generally looking at the entire devices for any scratches, holes, peeled stickers or other signs of someone messing with the asset.
Inspecting the environment near the device is important as well.
Reviewing the area around the asset, looking for signs that remote cameras have been installed and/or if there are unexpected charity boxes or merchandising that could be hiding bluetooth skimmers will further ensure the safety and security of your devices.
Recording the data around inspections.
Finally, whether you choose to use a log book, excel spreadsheet, or other tool, you'll want to collect and recording the inspection data and results of each inspection. At a minimum you should be recording:
- Who inspected the device
- The location of the inspection
- The date and time
- Confirmation of the asset's unique identifier
- Answers to inspection questions
- Comments on any inconsistencies or concerns
Ultimately, you want to be able to provide all of this data to your QSA to prove your compliance and be able to track down the source of an incident, if one ever occurs.
Next week, I'm going to cover the final piece of the requirement, 9.9.3 which covers policy and training around the inventory and inspections.
Header image by nolifebeforecoffee, used under CC 2.0